Breadcrumbs
Home / Wireless Network Modded to See Through WallsWireless Network Modded to See Through Walls
Last Updated on Sunday, 29 November 2009 10:01 Written by DarkKnightH20 Saturday, 3 October 2009 12:00
Okay, this isn’t as cool as it sounds, but is still cool nevertheless. It’s actually a concept I had thought about too, so I’m glad it has come into fruition (though I feel as if I should have done something on this first!). As you may know, signal strength varies as people move around in a room. This can help you track the movements of people.
“The way signal strength varies in a wireless network can reveal what’s going on behind closed doors.
It’s every schoolboy’s dream: an easy way of looking through walls to spy on neighbors, monitor siblings, and keep tabs on the sweet jar. And now a dream no longer…
Researchers at the University of Utah say that the way radio signals vary in a wireless network can reveal the movement of people behind closed doors. Joey Wilson and Neal Patwari have developed a technique called variance-based radio tomographic imaging that processes the signals to reveal signs of movement. They’ve even tested the idea with a 34-node wireless network using the IEEE 802.15.4 wireless protocol, the protocol for personal area networks employed by home automation services such as ZigBee.
The basic idea is straightforward. The signal strength at any point in a network is the sum of all the paths the radio waves can take to get to the receiver. Any change in the volume of space through which the signals pass, for example caused by the movement of a person, makes the signal strength vary. So by “interrogating” this volume of space with many signals, picked up by multiple receivers, it is possible to build up a picture of the movement within it.
In tests with a 34-node network set up outside a standard living room, Wilson and Patwari say they were able to locate moving objects in the room to within a meter or so. That’s not bad, and the team says there is ample potential for improvement by increasing accuracy while reducing the number of nodes.
The advantage of this technique over others is, first, its cost. The nodes in such a network are off-the-shelf and therefore cheap. Other through-wall viewing systems cost in excess of $100,000. The second advantage is the ease with which it can be set up. Wilson and Patwari say that adding a GPS receiver to each node allows it to work out its own location, which should dramatically speed up the imaging process. Other systems have to be “trained” to recognize the environment.
Wilson and Patwari have even worked out how their system might be used:
“We envision a building imaging scenario similar to the following. Emergency responders, military forces, or police arrive at a scene where entry into a building is potentially dangerous. They deploy radio sensors around (and potentially on top of) the building area, either by throwing or launching them, or dropping them while moving around the building. The nodes immediately form a network and self-localize, perhaps using information about the size and shape of the building from a database (eg Google maps) and some known-location coordinates (eg using GPS). Then, nodes begin to transmit, making signal strength measurements on links which cross the building or area of interest. The received signal strength measurements of each link are transmitted back to a base station and used to estimate the positions of moving people and objects within the building.”
That’s ambitious, but if they do get their system to the point where it can be used like this, it raises another problem: privacy.
How might such cheap and easy-to-configure monitoring networks be used if they become widely available? What’s to stop next door’s teenage brats from monitoring your every move, or house thieves choosing their targets on the basis that nobody is inside?
Of course, in the cat-and-mouse game of surveillance, it shouldn’t be too hard to build a device that disables such a monitoring network. But only if you know it’s there in the first place.
There are fun and games galore to be had with this idea.”
Source: Technology Review
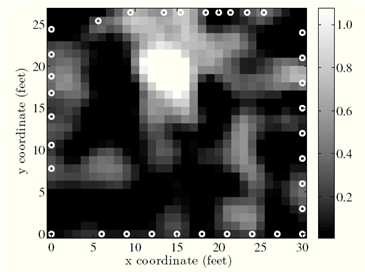
The resolution possible with this technology is great for planning tactical missions in unfamiliar buildings for hostage rescue, like the earlier idea in the article. Let’s hope the resolution doesn’t improve all that much beyond what’s currently capable right now, otherwise we will see mischievous folk and creepers lining up to set up these networks.